Introduction
The increasing adoption of cyber-physical and connected objects promises to address a large variety of societal challenges, from simplifying human communications (with legal authorities, public and private communications) to supporting next generation industry (so called Industry 4.0), smart cities and transportations. Since these computing objects become more and more integrated into our daily lives, their physical access is also becoming easier for malicious users.
However, such systems, in particular cost-driven ones such as Internet-of-Things (IoT) nodes, are vulnerable to a wide range of cyber-attacks. In addition to usual networked systems’ threats, computations are vulnerable to a large range of physical attacks, which exploit some characteristics of the target system including both software and hardware. Among these, side-channel attacks (SCA) can infer secret information from physical observations measured during the execution of sensitive computations. SCA typically exploit physical quantities such as electromagnetic signature and power consumption, behaviour of cache memories, and effects due to speculative execution. SCA have gained momentum with the increased use of cryptography because they represent, with fault injection attacks, the most effective way to break implementations of cryptography.
Many software or hardware protections have been proposed to harden systems vulnerable to side-channel attacks. These protections aim either to make any computation independent of sensitive data (masking techniques) or to introduce enough noise (e.g. inserting random delays, shuffling instructions of parallelisable tasks or inserting dummy instructions) to make sensitive data retrieval too difficult from an attacker perspective (hiding technique).
To ease the heavy and costly hardening process, several automated techniques have been proposed to either analyse or protect software or hardware implementations. These techniques rely on an abstraction model of the target architecture and the potential source of leakage (e.g. source code or assembly level) that is simple enough to keep them tractable. However, the lack of precision of such models and the need to better model the target implementation has been recently highlighted in the litterature: hardened systems are vulnerable to side-channel attacks due to leakage at the micro-architecture layer.
Main objectives and expected results
The IDROMEL project aims to contribute to the design of secure systems against side-channel attacks based on power and electromagnetic observations, for a wide range of computing systems, from cost-effective ones implemented in IoT devices to more complex architectures commonly integrated into mobile phones. IDROMEL will investigate the impact of the processor micro-architecture on power and electromagnetic side-channel attacks as a key concern for the design of secure systems. The objective of the project is to provide security assessments and automated security tools that take into account the target micro-architecture, as well as to design new processors that integrate hardware countermeasures.
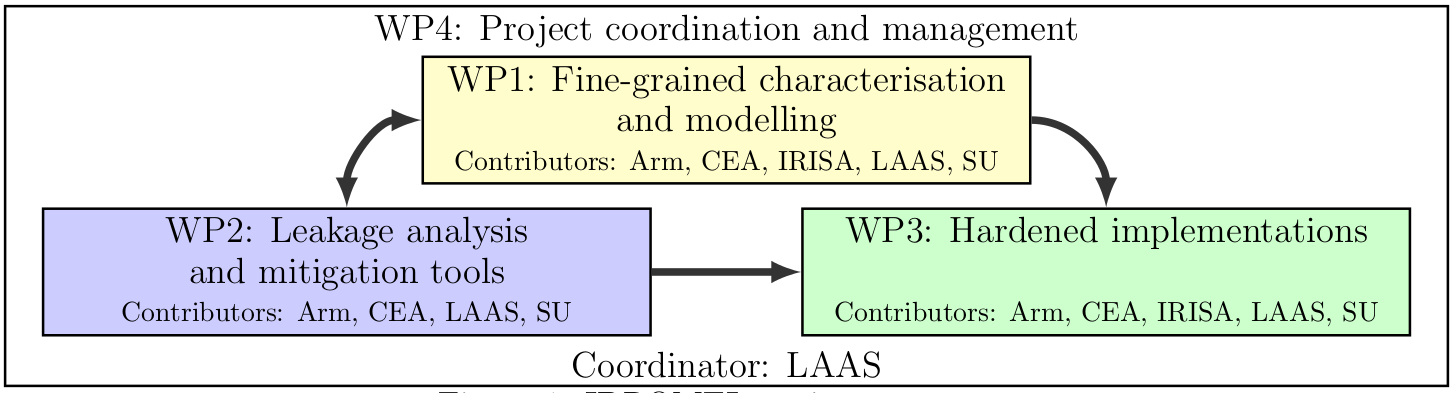
In order to achieve this objective, IDROMEL will follow a bottom-up approach starting with the development of characterization methods and models taking into account micro-architectural details (WP1), the design of leakage-tracking and mitigation tools (WP2) to support the hardening of both software and hardware implementations (WP3). The structure of the project is provided in Figure 1. The expected results of the project are as follows:
- Leakage sources characterization: a methodology to evaluate leakage sources from detailed description of the micro-architecture (grey-box approach) or from public information (black-box approach), with reproducible characterization based on public test vectors;
- Security assessment methods: formal code verification, leakage simulators and vulnerability analysis;
- Automated security tools: a compiler for the application of software countermeasures;
- Hardware hardening techniques: configurable design technique for the application of hardware countermeasures.
Tasks
WP1
T1.1 Leakage sources characterization
T1.2 Leakage source vulnerability analysis
T1.3 Public test vector benchmark
WP2
T2.1 Hardware tools
T2.2 Software tools
WP3
T3.1 Hardened processors
T3.2 Hardened software libraries
WP4
T4.1 Project management
T4.2 Dissemination
Milestones
M0 Kickoff meeting
T0+0
M2 First version of the analysis and mitigation tools
T0+21
M1 Achievement of Consortium agreement
T0+12
M3 Second version of the analysis and mitigation tools
T0+39